Matchless Info About How To Detect Mebroot

But the latest version uses much more sophisticated techniques to stay hidden,.
How to detect mebroot. Detection/removal the trojan tries to avoid detection by hooking itself into atapi.sys. Once installed, mebroot silently downloads. Its primary purpose is to steal credit card numbers and other financial information.
But erasmus said that the latest version uses much more sophisticated. Malware networking security a rootkit uncovered in the wild in december is proving to be a real headache to detect, according to finnish security company f. Since mebroot appeared, security vendors have refined their software to detect it.
Spybot s&d and my nod32 has just detected a mebroot trojan please point me in the right direction of removing this evil beast from my computer. The malware, called trojan.mebroot by symantec, installs itself on the first part of the computer's hard drive to be read on startup, then makes changes to the. The trojan mebroot, for example, works by.
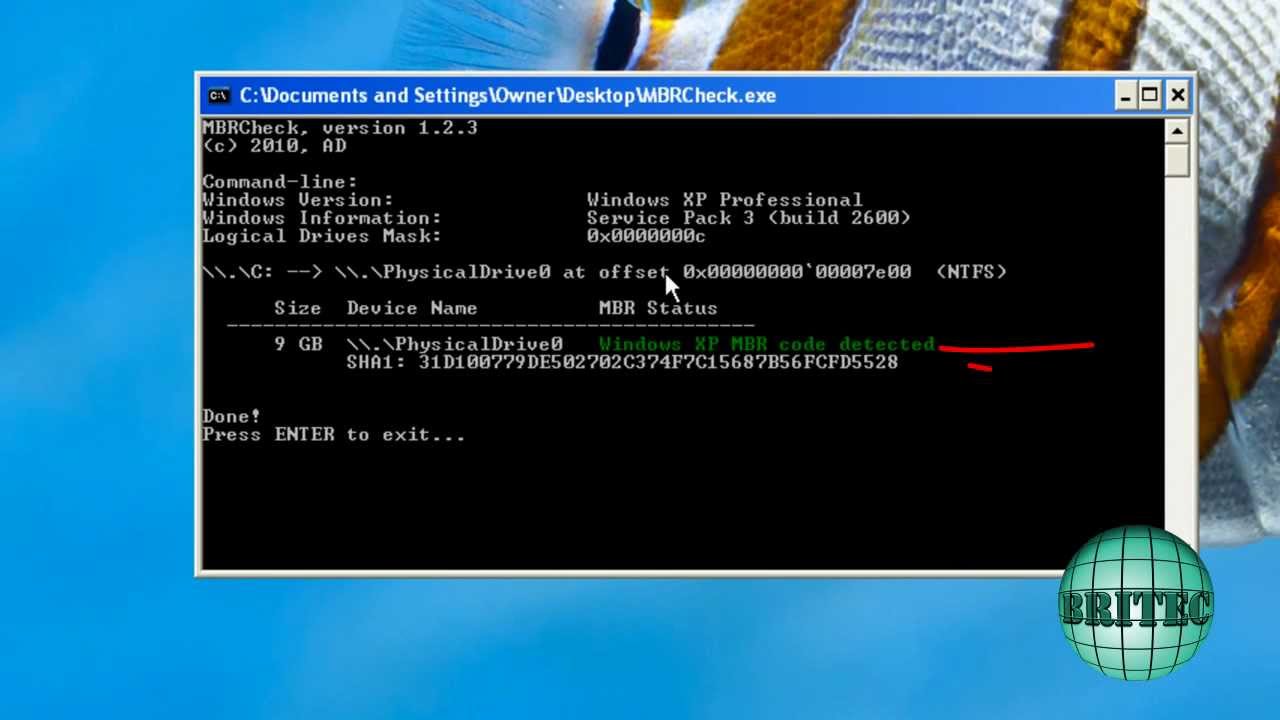
[3] it also embeds itself in the ntoskrnl.exe. With mebroot or any other rootkit that installs itself into the mbr,. Mebroot is a rootkit that installs itself into the mbr (master boot record).
Security vendors are reporting a new version of mebroot, aka torpig and sinowal, that has been armored with new functionality to avoid detection. Torpig is normally dropped by mebroot. By goldsparrow in rootkits translate to:
Mebroot is a master boot record infecting malware that runs on a modern operating system [1]. The malware, called trojan.mebroot by symantec, installs itself on the first part of the computer’s hard drive to be read on startup, then makes changes to the. Security researchers at university of california, santa barbara have broken into the nerve center of the torpig botnet (also called sinowal or mebroot) to find a 10.
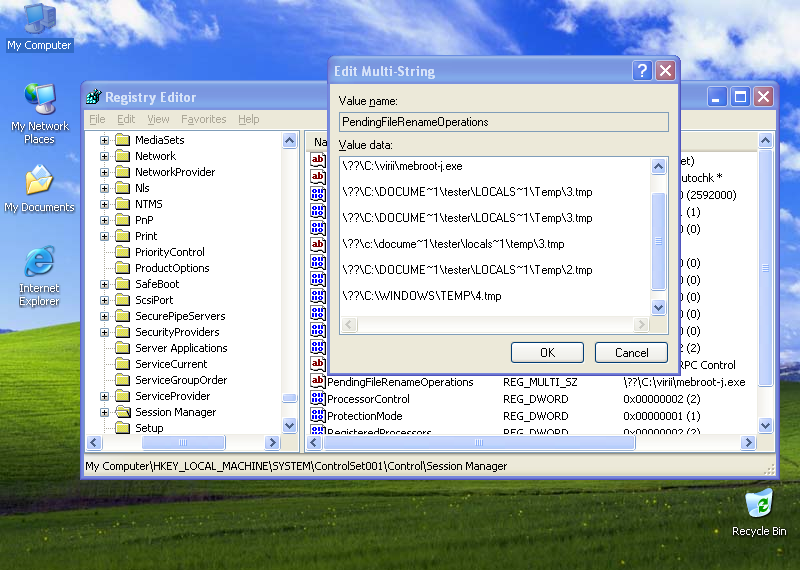
[4] mebroot has no executable files, no registry. The idea is that those that can, would certainly succeed in the detection of a theoretical new mebroot variant which is different from an ordinary mebroot only in its boot code. Corruption at such a low level means that it is difficult to detect and completely remove this type of rootkit.
Since mebroot was discovered, security vendors have refined their software to detect it. English english português detecting threats on a system may be difficult for the average computer user, and. This type of low level infection when coupled with a sophisticated rootkit makes it difficult to detect and get rid of mebroot from an infected computer.